Github Action with Azure
In this post, I will demonstrate a pipeline that is triggered only when code is pushed to the testing or main branch. The pipeline includes static code analysis, unit testing, and an image vulnerability scan. After these checks, the container image is deployed to Azure Kubernetes Service (AKS).
Proccess
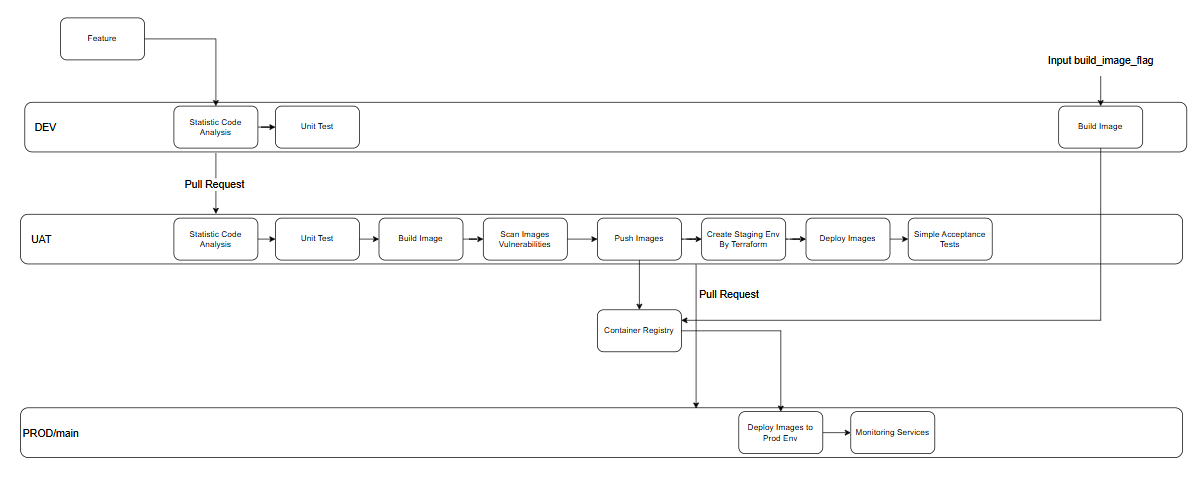
Code Repo
Features
- Dev Backend Code checks - Code Analysis, Test
- UAT Backend CI - Test, Build, and Deploy to UAT
- PROD Backend CD - Deploy Backend Services to AKS
- PROD Frontend CI & CD
Prerequirements
- An Azure account with a credit limit
- Install Terraform
Step 1: Initialize Production Env by Terraform
1 | cd terraform/production/ |
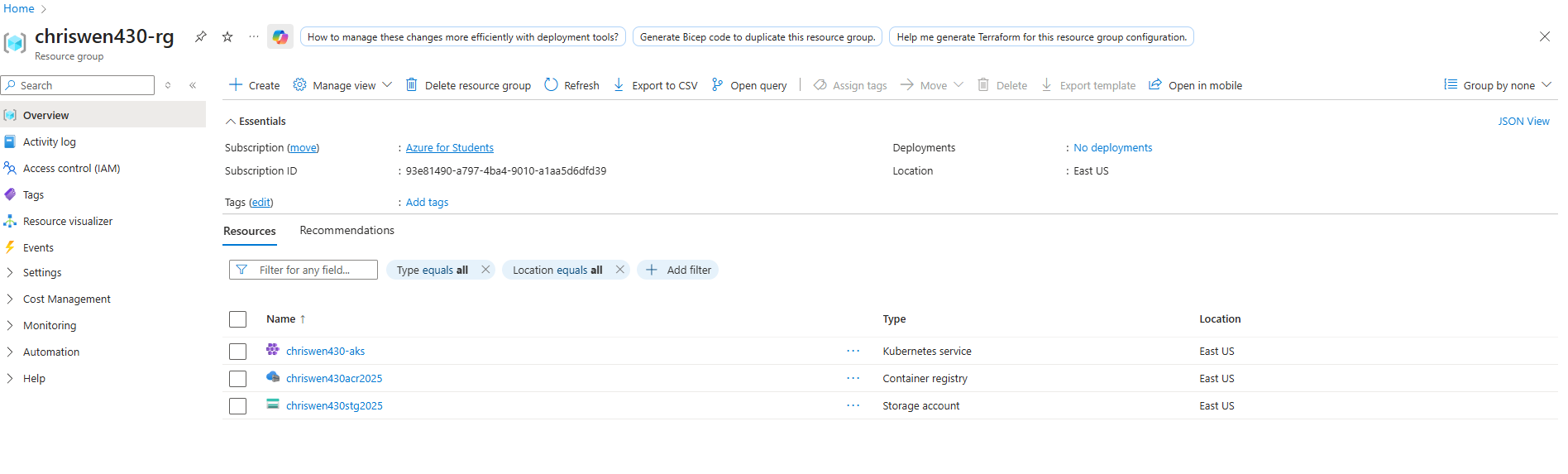
Step 2: Collect relevant information
Get Storage Account key1
az storage account keys list --resource-group chriswen430-rg --account-name chriswen430stg202507 --output table
Get container registry info1
2
3
4
5az acr show --name chriswen430acr202507 --resource-group chriswen430-rg --query id --output tsv
az acr show --name chriswen430acr202507 --resource-group chriswen430-rg --output table
az acr credential show --name chriswen430acr202507 --resource-group chriswen430-rg --query "username" -o tsv
az acr credential show --name chriswen430acr202507 --resource-group chriswen430-rg --query "passwords[0].value" -o tsv
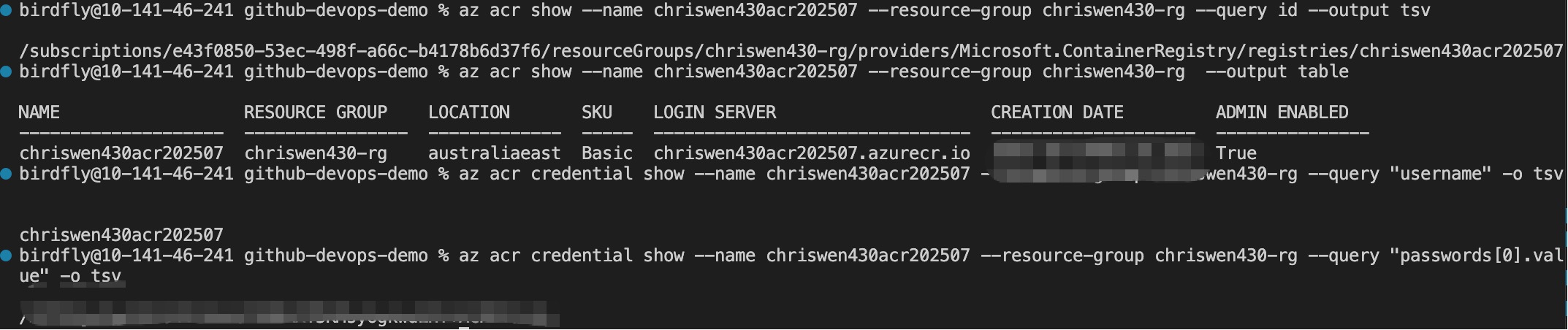
Create Service Principal for GitHub Action1
az ad sp create-for-rbac --name "github-action-sp" --role Owner --scope /subscriptions/e43f0850-53ec-498f-a66c-b4178b6d37f6/resourceGroups/chriswen430-rg --sdk-auth
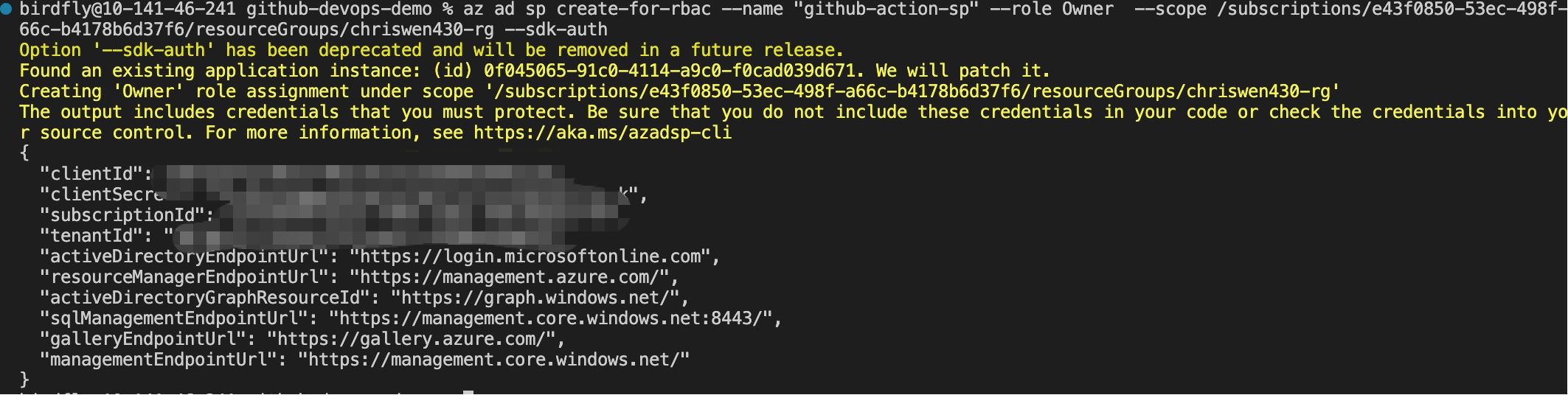
Step 3: Configure GitHub Secrets
Step 5: Test Pipeline
Dev Backend Code checks - Code Analysis, Test
- File Path: .github/workflows/dev-backend.yml
- Main Steps:
- Step 1: Code Quality Checks and Unit Tests
- Static Code Analysis by flake8
- Unit Test
- Step 2: Build Image and Scan Vulnerabilities
- Build Docker Image
- Scan Image Vulnerabilities by Trivy
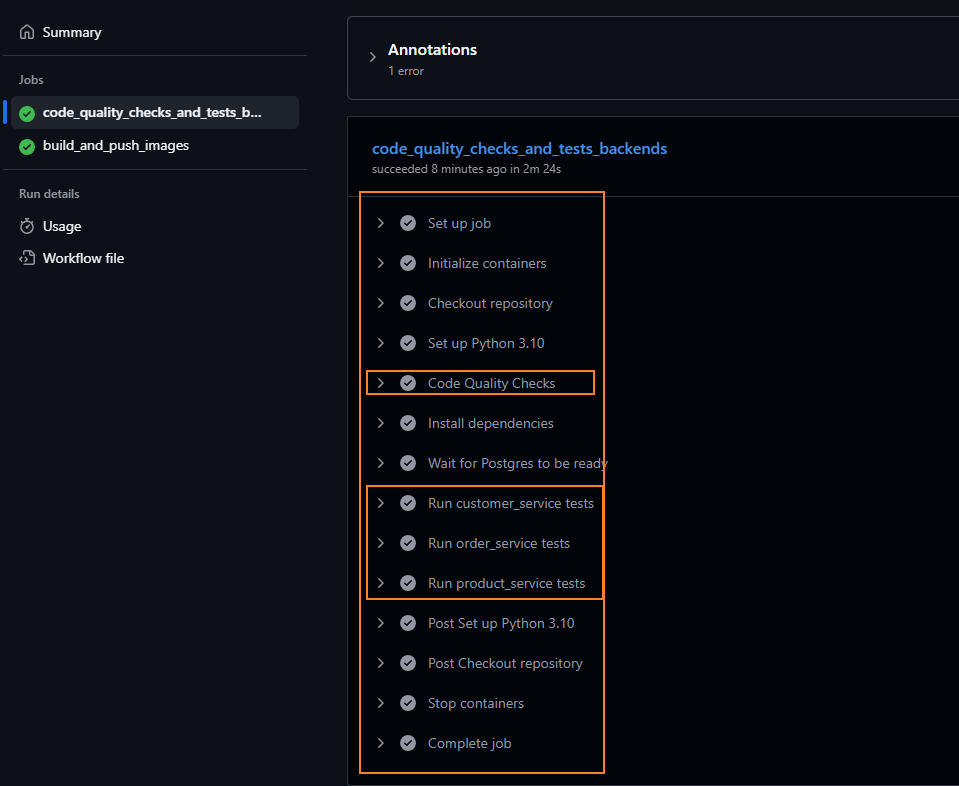
- Step 1: Code Quality Checks and Unit Tests
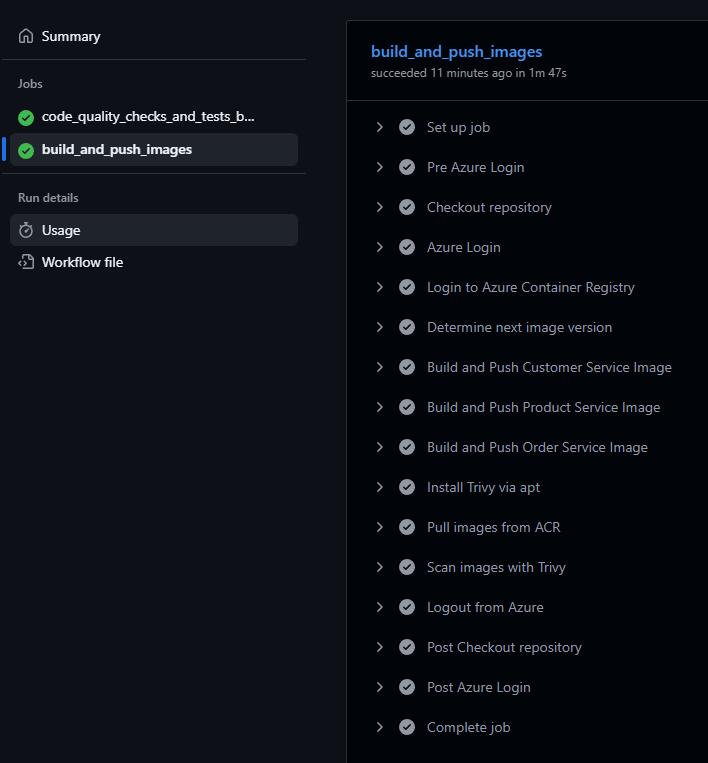
UAT Backend CI - Test, Build, and Deploy to UAT
- File Path: .github/workflows/uat-backend-ci.yml
- Main Steps:
- Step 1: Code Quality Checks and Unit Tests
- Step 2: Build Image and Scan Vulnerabilities
- Step 3: Create Simulated Env to Test Deployment
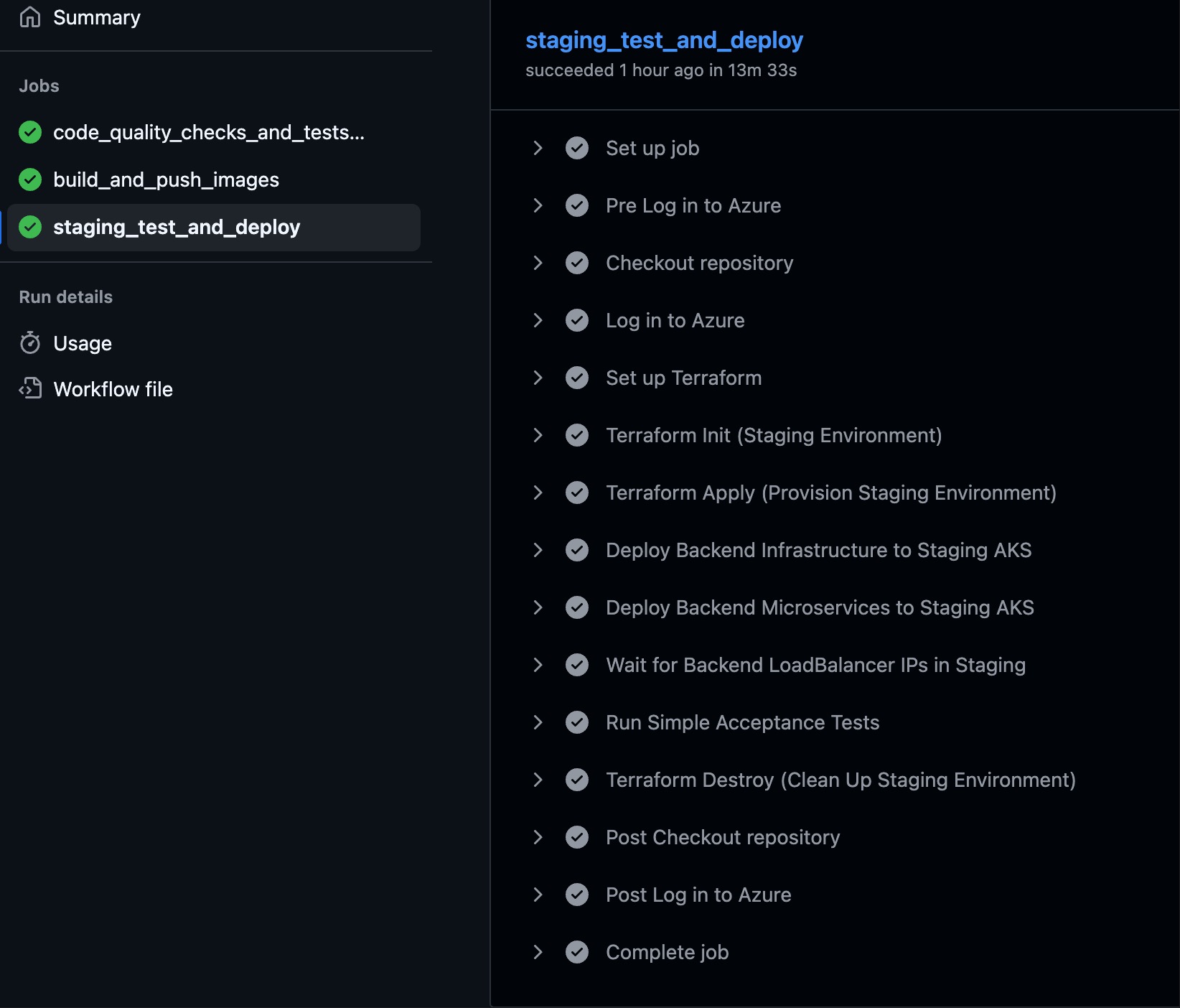
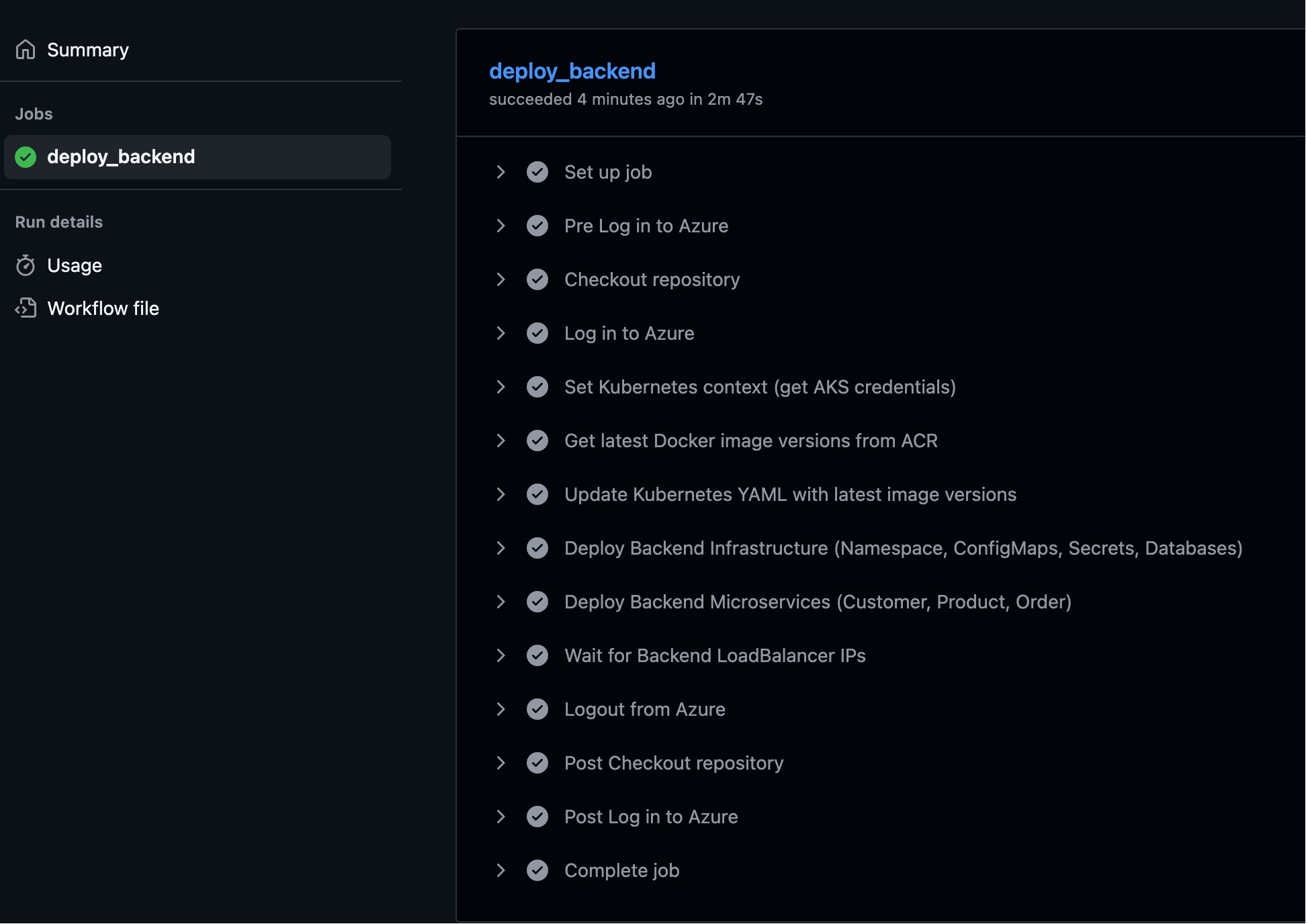
PROD Backend CD - Deploy Backend Services to AKS
- File Path: .github/workflows/prod-backend-cd.yml
- Main Steps:
- Step 1: Build and Push Image to ACR
- Step 2: Update Kubernetes Configuration with New Image
- Step 3: Deploy Backend Infrustructure
- Step 4: Deploy Backend Services
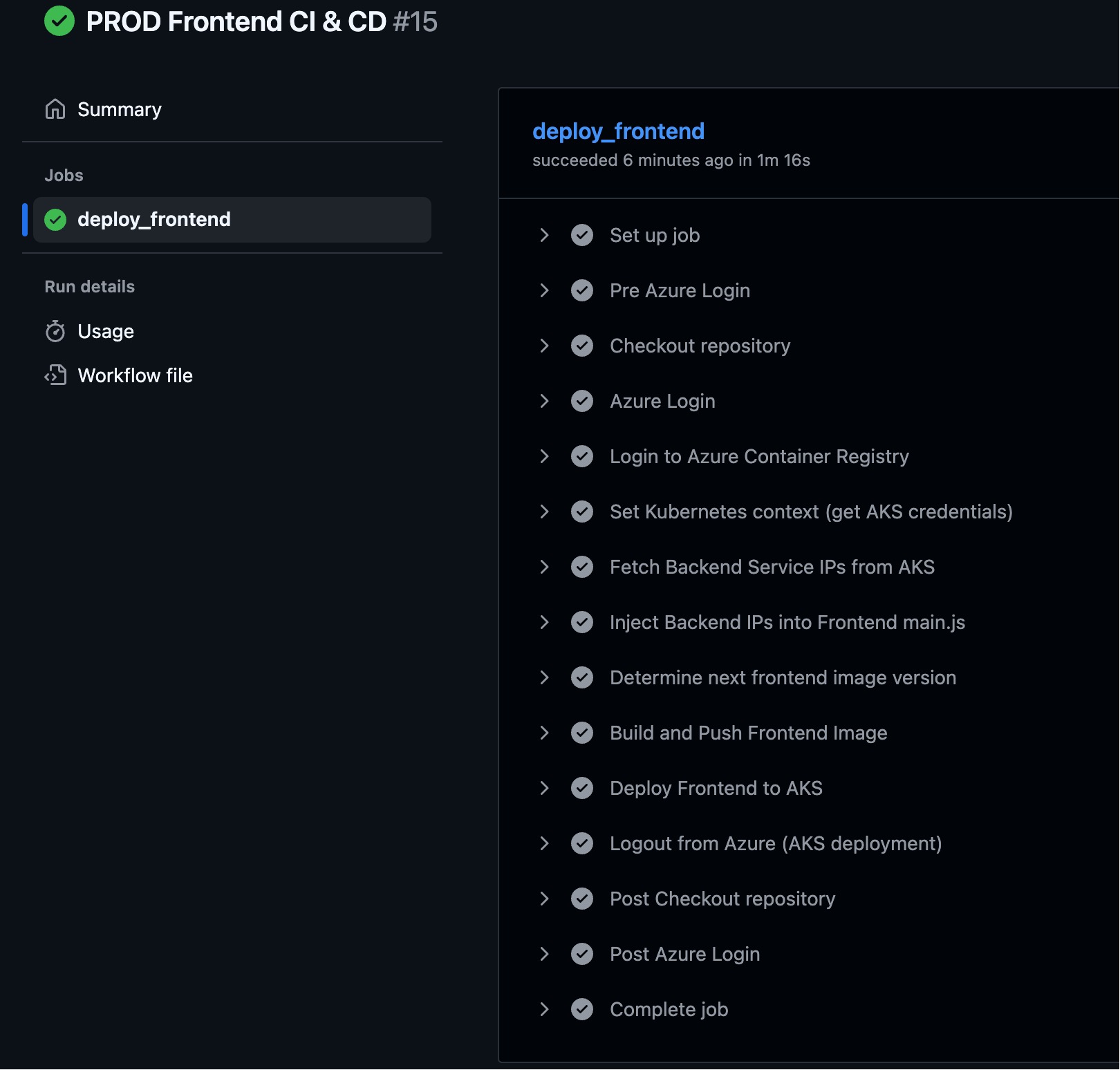
PROD Frontend CI & CD
- File Path: .github/workflows/prod-frontend-ci&cd.yml
- Main Steps:
- Step 1: Build and Push Image to ACR
- Step 2: Update Kubernetes Configuration with New Image
- Step 3: Deploy Frontend Service
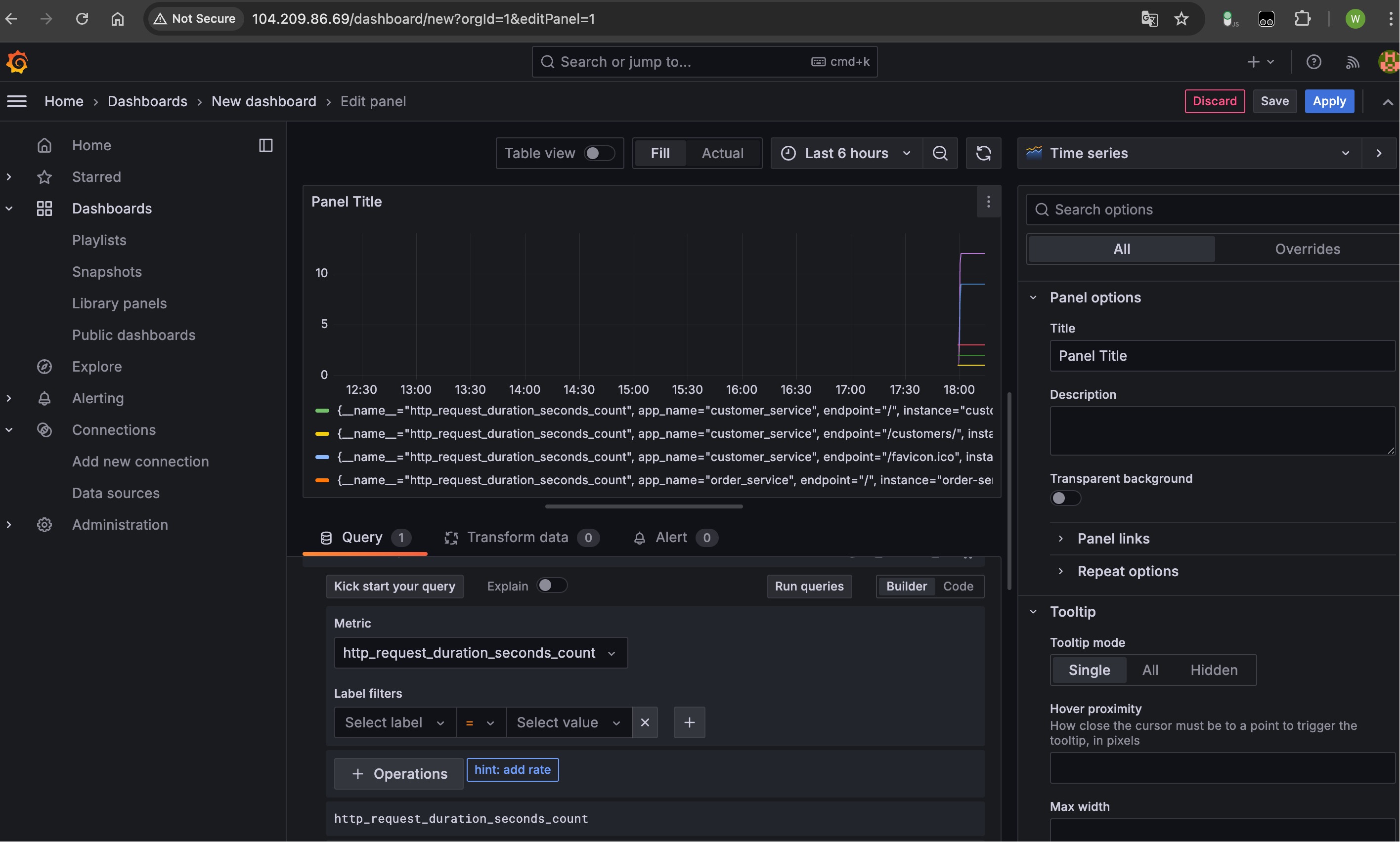
Step 6: Create Promethus and Grafana Dashboards
prerequisties: connect to AKS cluster
create promethus and grafana1
2kubectl apply -f prometheus-configmap.yaml -f prometheus-deployment.yaml -f prometheus-rbac.yaml
kubectl apply -f grafana-deployment.yaml 
Set Connections
Set Metrics